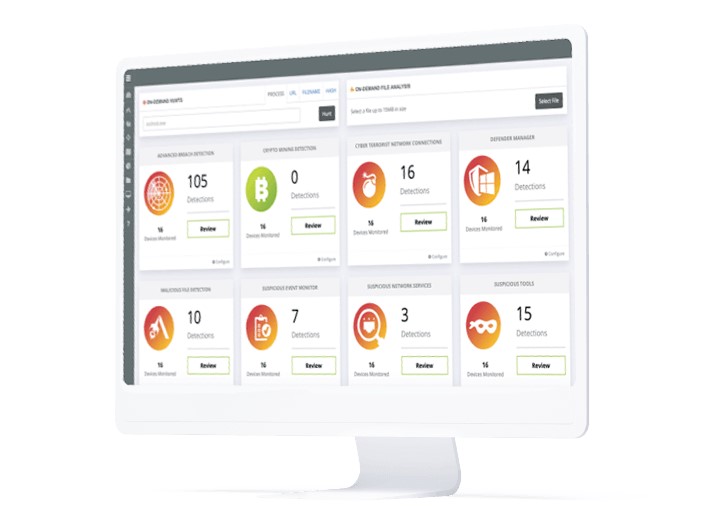
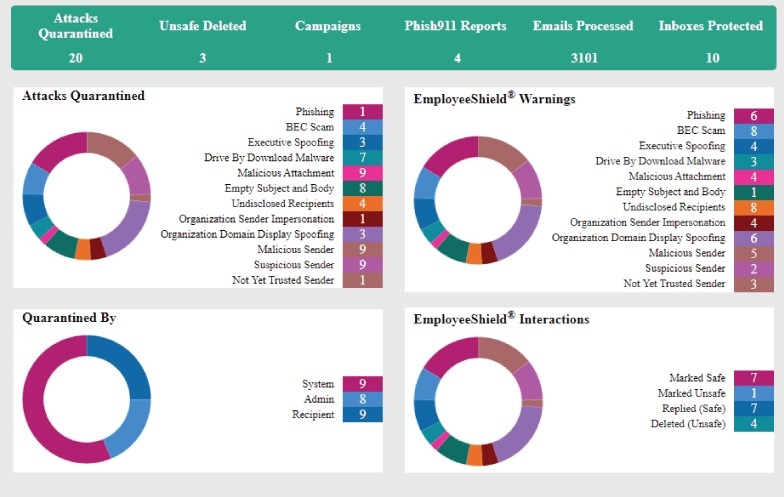
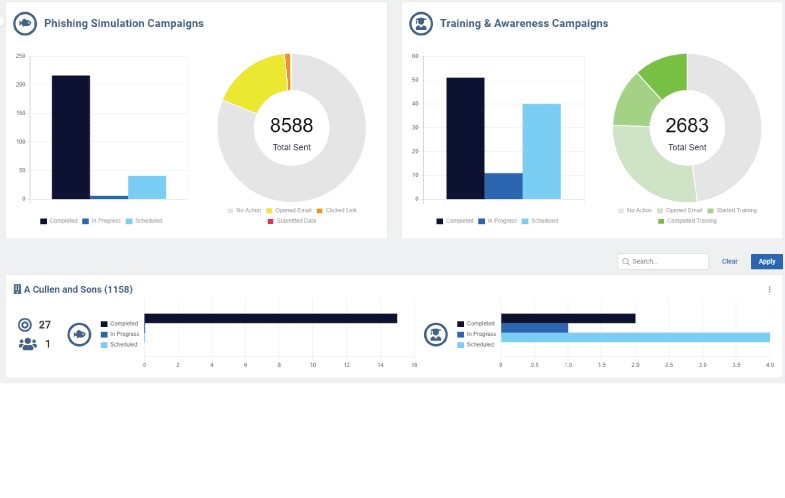
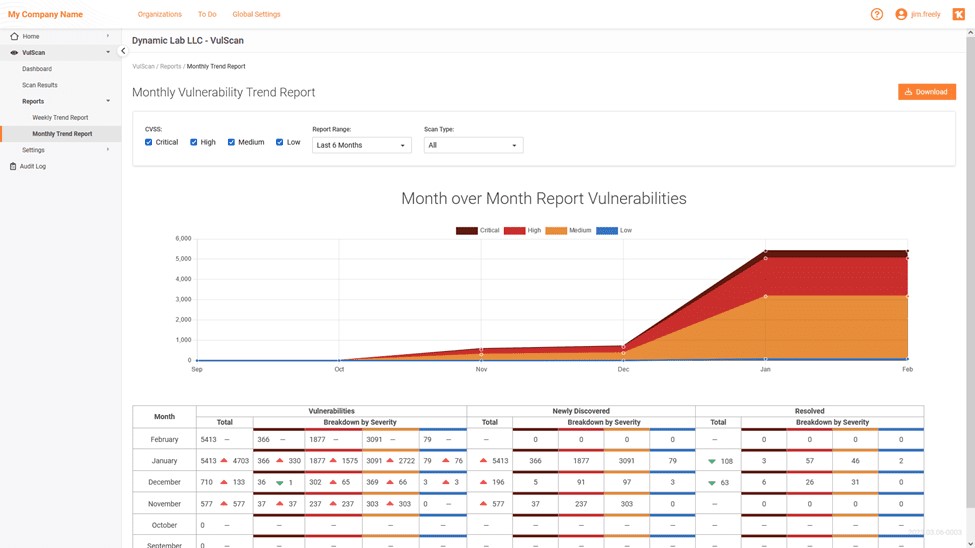
• Endpoint
Windows, macOS and Linux event log monitoring, breach detection, malicious files and processes, threat hunting, intrusion detection, 3rd party NGAV integrations and more.
• Network
Firewall and edge device log monitoring integrated with threat reputation, whois and DNS information.
• Cloud
Microsoft 365 security event log monitoring, Azure AD monitoring, Microsoft 365 malicious logins, Secure Score.